HTTP Strict-Transport-Security (HSTS)
The VIP Platform supports and strongly encourages the use of the HTTP Strict-Transport-Security response header (HSTS). This header informs browsers that a site should only be accessed using HTTPS , and that any future attempts to access the site using HTTP will automatically be converted to HTTPS.
HSTS is an important security measure that prevents person-in-the-middle attacks, protocol downgrade attacks, and cookie hijacking.
Limitations
Before enabling an HSTS policy, verify that the following limitations are acceptable:
- The HSTS feature is enabled and configured per-environment; not per-domain.
- If HSTS is enabled for an environment, but a site’s domain mapped to that environment does not support HTTPS—or if support for HTTPS is discontinued for that domain in the future—visitors will not be able to access the site the domain is pointed to. This is not a bug; this is how HSTS is designed to work.
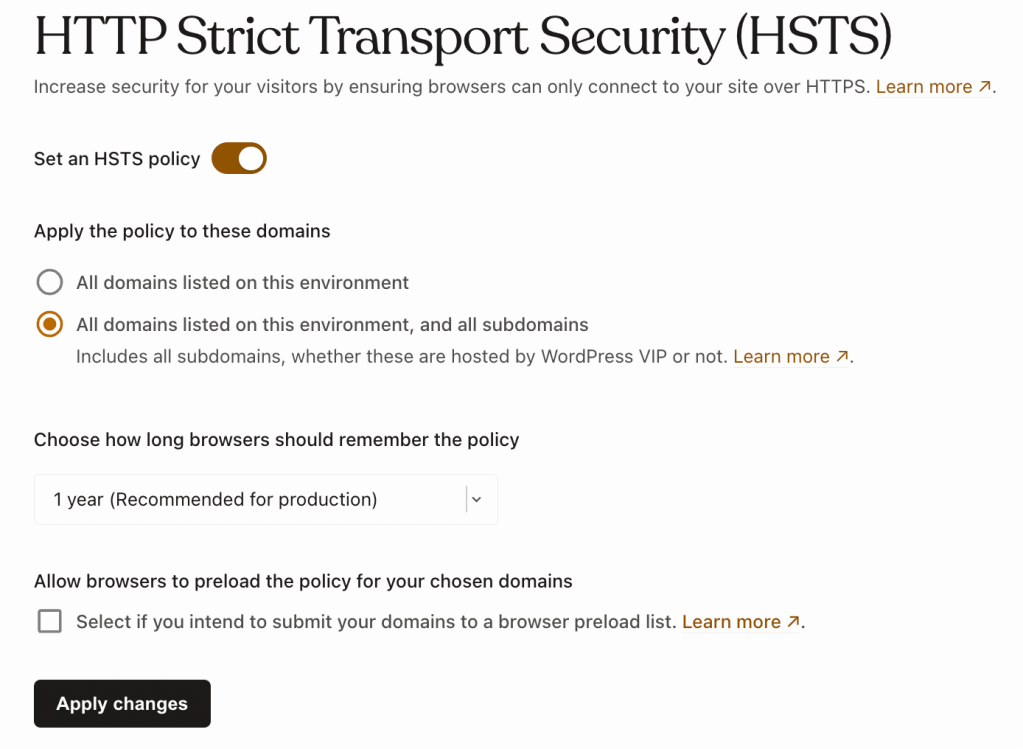
Enable HSTS for an environment
Prerequisite
To edit HSTS settings, a user must have at minimum an Org admin role or an App admin role for that application.
Changes made to HSTS settings will take up to 10 minutes to be applied to that environment.
- Navigate to the application view of the VIP Dashboard.
- Select an environment from the environment dropdown located at the upper left of the VIP Dashboard to which the settings will apply.
- Select “Domains & TLS” from the sidebar navigation at the left of the screen.
- Select “HSTS” from the submenu.
- Toggle the Set an HSTS policy option to “on”.
- Edit the available setting options in the HTTP Strict Transport Security panel.
- Select “Apply changes” to save the edited settings.
Domains included in the HSTS policy
- All domains: By default, when enabled, HSTS will be applied to all custom domains that are added to an environment.
- All domains and their subdomains: This option will apply HSTS to all custom domains that are added to an environment as well as their subdomains; even for subdomains that are not added to the environment or pointed to VIP.
Note
Before enabling this option, verify that all subdomains support HTTPS.
Length of time browsers should remember the HSTS policy
This setting determines the value of the HSTS header’s max-age parameter. The value assigned to the max-age parameter tells a browser the amount of time that a site should only be accessed using HTTPS.
- 5 minutes: Select this option in order to verify that all domains (and subdomains if applicable) associated with the environment support HTTPS. Complete this verification process prior to enabling HSTS for a 1 year duration.
- 1 year: Select this option after verifying that all domains (and subdomains if applicable) associated with the environment support HTTPS. An HSTS policy set to 1 year expiration cannot be disabled before that year expires without risk of blocking site access for visitors that have already set the HSTS
max-ageparameter in their browsers. HSTS should only be set to a 1 year expiration if a commitment can be made to supporting HTTPS for the affected domains and subdomains for that period of time.
Allow browsers to preload the HSTS policy
Browsers maintain a hardcoded “preload” list of domains that are only accessible with HTTPS. Without preloading, a browser will only enforce HTTPS after a user’s first visit to a site with HSTS enabled (when the header is first seen by their browser). This means a visitor’s first visit to a site does not have the protection of HSTS. Preloading guarantees that all visits to that site—including the first visit—for all visitors are protected by HSTS.
Note
It can be difficult to for a domain to be removed from the preload list. Only pursue this option if a commitment can be made to supporting HTTPS for the affected domains and subdomains indefinitely.
Domains are eligible to be added to a browser’s list if they have:
- A 1 year HSTS policy applied to that domain, as well as all of its subdomains.
- A
preloadparameter set in the domain’s HSTS header.
To add a domain to a browser’s preload list:
- When enabling HSTS in the VIP Dashboard, select the option to apply the policy to “All domains listed on this environment, and all subdomains”.
- Select the 1 year HSTS policy in order to access the additional “preload” option below it.
- Select the “preload” option in order to add the
preloadparameter to a domain’s HSTS header. - Select “Apply changes” to save the edited settings.
- Submit the eligible domain to Chrome’s HSTS Preload List Submission intake form. Many browsers use the preload list maintained by Chrome.
It can be difficult to for a domain to be removed from the preload list. Only pursue this option if a commitment can be made to supporting HTTPS for the affected domains and subdomains indefinitely.
Disable HSTS for an environment
Sites that have an HSTS policy set to a 1 year expiration should not remove support for HTTPS access to that site for at least a year after HSTS is disabled. The max-age value of a site’s HSTS header policy is recognized per-browser per-user. The first time a user visits a site that has an active HSTS policy, the max-age value for that HSTS header for that site is set in the user’s browser. From that date, the browser will only allow the user to access that site by HTTPS for a full year after that visit, even if HSTS for that site is disabled before that year expires for the user.
Changes made to HSTS settings will take up to 10 minutes to be applied to that environment.
- Navigate to the application view of the VIP Dashboard.
- Select an environment from the environment dropdown located at the upper left of the VIP Dashboard to which the settings will apply.
- Select “Domains & TLS” from the sidebar navigation at the left of the screen.
- Select “HSTS” from the submenu.
- Toggle the Set an HSTS policy option to “off”.
- Select “Apply changes” to save the edited settings.
Last updated: March 07, 2025