Vulnerability and Update Scan by the VIP Code Analysis Bot
Vulnerability and Update Scans are an integration of Codebase Manager with the VIP Code Analysis Bot (the Bot). Vulnerability and Update Scans by the Bot scan pull requests made to an application’s wpcomvip GitHub repository. The Bot queries the WPScan API for known plugin and theme security vulnerabilities and available version updates.
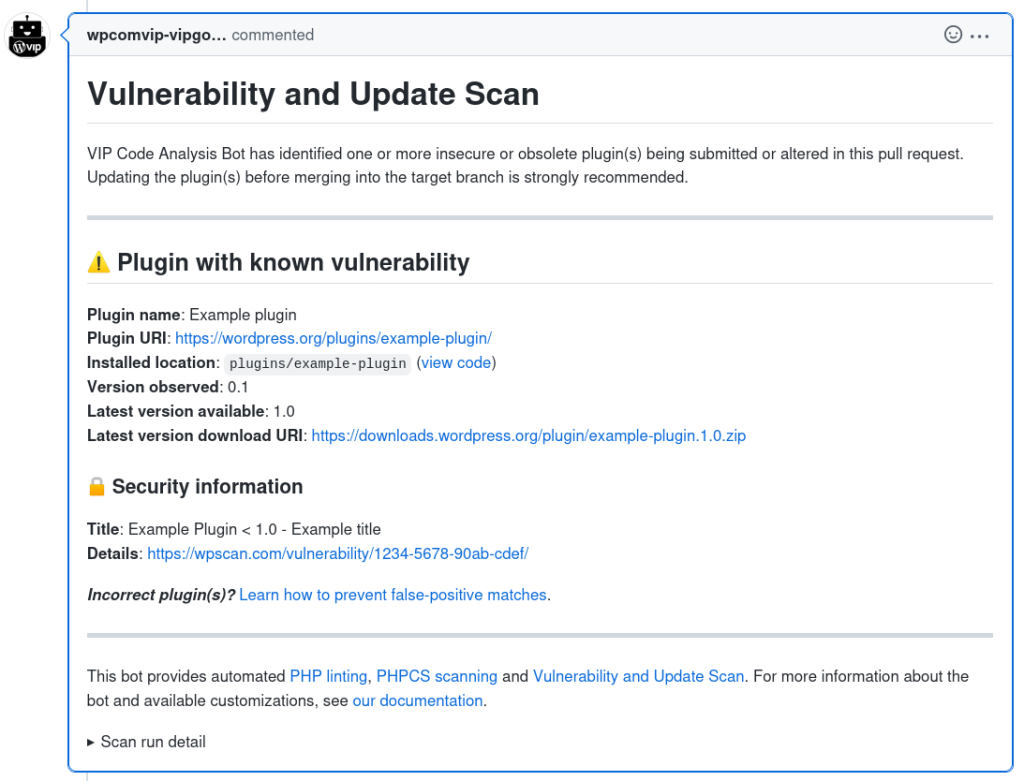
If the Bot detects a plugin or theme being added or altered in a pull request that has a known vulnerability or available version update, it will generate feedback and report the known vulnerabilities or out of date plugins or themes.
Vulnerability and Update Scans are intended to detect security issues and available version updates before plugins and themes are deployed—or when they are being altered in some way.
Once Plugins are deployed they will be frequently scanned for known vulnerabilities and available updates, and any issues and updates found will be reported in the Plugins panel of the VIP Dashboard.
Default behavior
Only plugins and themes located in the /plugins, /client-mu-plugins, and /themes directories in the root of the application’s GitHub repository will be scanned by the Bot’s Vulnerability and Update Scan.
- Adding a plugin or a theme via pull request will trigger the Bot’s Vulnerability and Update Scan.
- Updating an existing plugin or a theme via pull request will trigger the Bot’s Vulnerability and Update Scan.
- Removal of a plugin or theme’s files via pull request will not trigger the Bot’s Vulnerability and Update Scan for that plugin/theme.
When triggered, the Bot will scan a pull request to identify which plugins or themes have been added or altered. The Bot will collect the plugin or theme headers found to be altered and compare those to the WordPress.org API for plugins and for themes. “Slugs” for successfully identified matches are collected, and then used to query the WPScan API. The Bot will report if the information retrieved from the WPScan API indicates that the version of a plugin or theme being added or altered in a pull request has known vulnerabilities or available version updates.
Follow the recommendations to prevent Codebase Manager from identifying a false positive match due to the naming convention of a plugin or theme directory.
Information included in Bot feedback
Pull requests that receive Vulnerability and Update Scan feedback from the Bot will include the following information in the pull request description field:
- Plugin or theme name
- Plugin or theme URI: Source URL of the reported vulnerable plugin in the WordPress.org Plugin Directory or theme in the WordPress.org Theme Directory.
- Installed location: Path to the directory in the GitHub repository branch matching the reported vulnerable plugin or theme.
- Version observed: The version of the plugin or theme in the pull request.
- Latest version available: The most current available version of the plugin or theme.
- Latest version download URI: WordPress.org source URL for download of the most current version of a plugin or theme.
VIP strongly recommends acting on the Bot’s feedback when a known vulnerability is reported or when a version is out of date by updating a plugin or theme to the “Latest version available“.
Skipping Vulnerability and Update Scans
It is possible to configure the Bot to skip Vulnerability and Update Scans of a particular pull request by applying the skip-wpscan label to a pull request before analysis starts.
The Bot can also be configured to skip analysis of specific directories by creating a file named .vipgoci_wpscan_api_skip_folders in the relevant branch. Directories that are listed in this file, and the files that exist within them, will be ignored by the Vulnerability and Update Scans.
Vulnerability and Update Scans by the Bot can be completely disabled for a branch—or repository—by configuring the wpscan-api option in the .vipgoci_options file.
Last updated: December 22, 2023