IP Restrictions
The IP Restrictions panel in the VIP Dashboard allows IP addresses—or ranges of IP addresses (aka subnets)—to be added to an “IP Allow List” or an “IP Deny List” for an application’s environment.
Allowing or denying requests from a specific group of IP addresses can be useful for sites with highly sensitive content, intranets, and non-production environments.
Configurations that are added to an environment’s “IP Allow List” or an “IP Deny List” apply to all requests, including requests that are:
- Cached or uncached
- From logged-in or anonymous users
- For static files, media files, REST API endpoints, or dynamically-generated content
- For a WordPress or a Node.js environment
Requests from services within Automattic’s networks require access to support the operation of a VIP application and are the only exception to the list of restricted requests above.
Limitations
- A maximum of 1,000 entries are allowed in an IP Restriction list. If a greater number of entries are required, create a Support request.
- An active IP Restriction List will also block content from Jetpack’s content distribution tools. To modify this behavior, review available options to Control Content Distribution via Jetpack.
- Configurations in an IP Restriction list might unintentionally block external services and tools that connect to an application. To resolve the issue, the entry’s configurations will need to be edited or removed altogether.
- Configurations in an “IP Allow List” or an “IP Deny List” might unintentionally block external services and tools that connect to an application. To resolve the issue, the list’s configurations will need to be edited or removed altogether.
- IP restrictions that are added to an environment must not block requests from the Automattic network or block site access for VIP Support. Blocking these requests—intentionally or unintentionally—might also block the ability for WordPress VIP to provide comprehensive support for a site(s) on that environment.
- If an environment is behind a reverse proxy, configurations added to IP Restrictions in the VIP Dashboard will not work as expected. Requests that are passed through a reverse proxy to a site on the VIP Platform have the remote IP address of the reverse proxy and not the IP address of the end user. IP restrictions must be configured at the reverse proxy level.
Access
Prerequisites
- To view the IP Restrictions for an environment, a user must have at minimum an App write role for that application or an Org member role.
- To edit the IP Allow List or the IP Deny List for an environment, a user must have at minimum an App admin role for that application or an Org admin role.
- A custom domain must have either a Let’s Encrypt or a custom TLS certificate installed in order for an IP Allow List to restrict access.
The IP Restrictions panel is located in the application view of the VIP Dashboard. Configurations added to IP Restrictions are environment-specific (e.g., production, develop).
- Navigate to the VIP Dashboard.
- Select the environment to which the settings should apply from the environment dropdown located at the upper left of the VIP Dashboard.
- Select “Security Controls” from the sidebar navigation at the left of the screen.
- Select “IP Address” from the submenu.
Existing entries for an environment’s IP Restrictions are in a table located in the main area of the panel.
IP Restriction list types
The options for an “IP Allow List” or an “IP Deny List” for an environment are displayed in the upper area of the IP Restrictions panel of the VIP Dashboard. The default setting for the IP Restrictions panel has the radio option for the “IP Deny List” toggled “on” and the list of restricted IP addresses is empty.
Only one IP Restriction list type—”IP Allow List” or an “IP Deny List”—can be active at a time.
IP Deny List
Access to an environment is denied for any incoming request that is from an IP address that matches an IP address on the environment’s “IP Deny List”. A 403 Forbidden error response will be returned by VIP’s CDN for denied requests.
IP Allow List
Access to an environment is only allowed for incoming requests that are from an IP address that matches an IP address on the environment’s “IP Allow List”. A 403 Forbidden error response will be returned by VIP’s CDN for all other requests.
Activating the “IP Allow List” list type does not block access to the environment until a minimum of one IP restriction entries has been added.
Enable the other IP Restriction list type
Note
The configurations of the previously enabled IP Restriction list type are deleted when a new IP Restriction list type is enabled.
- Select the radio option for the desired list type (“IP Allow List” or an “IP Deny List”). A dialog is generated to confirm the action of switching to the other list type.
- Select the button labeled “Copy” to add the configurations of the currently activated list type to the user’s clipboard. It is recommended to preserve the configurations in a local file where they can be retrieved in the future if needed.
- Select the button labeled “Confirm” to enable the other IP Restriction list type.
Add, edit, or remove IP Restriction entries
For both “IP Allow List” and “IP Deny List”, IP Restriction entries can be added, edited, or removed in either a form editor that has field prompts for values or in a text editor.
Updates made to an environment’s IP Restrictions typically take up to 10 minutes to take effect.
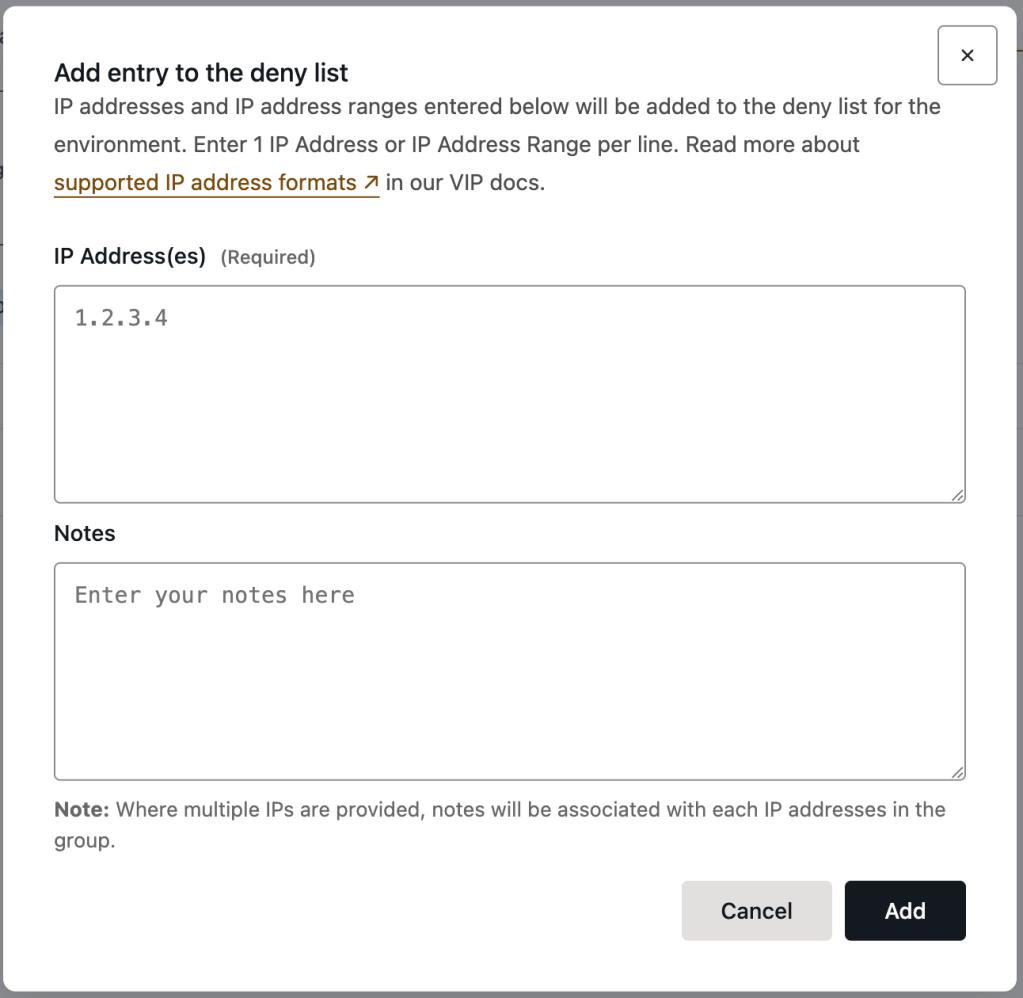
Add an entry
To add an IP Restriction entry or group of entries:
- Select the button labeled “+ Add” to enter the form editor dialog.
- Enter one ore more IP addresses to the field labeled “IP Address(es)“. Each entry must be added to a new line in the field.
- Optional: Add contextual information about the group of entries in the text field labeled “Notes“. The content added to this field will apply to all of the entries that are currently being edited.
- Select the button labeled “Add” to save the added configurations.
Edit an entry group
To edit an existing IP Restriction group:
- Select the linked text “Edit” located to the right of the existing entry group.
- Edit the configurations in the field labeled “IP Address(es)” or update the value of “Notes” for the group.
- Select the button labeled “Save” to save the updated IP Restriction configurations.
Remove an entry group
To remove an existing IP Restriction group:
- Select the trash can icon titled “Remove IPs” at the right of the row.
- Select the button labeled “Delete” in the dialog titled “Are you sure you want to delete the group?” to confirm the removal of the entry group.
Add, edit, or remove entry groups
Entries that are added or edited within the text editor must follow a specific syntax:
[IP Address/Range] #[Optional Note]
To add, edit, or remove IP Restriction entries in the text editor:
- Select the button labeled “Edit Full List”.
- To add entries, type or paste the IP address entries and optional notes into the text editor. Each entry must be added to its own separate line in the field. Ensure that every added IP address follows the supported IP address formats. Edit or remove entries in the text editor as needed.
- Select the button labeled “Save” to save the updated IP Restriction configurations.

Supported IP address formats
A combination of individual IPs and ranges of IP addresses (also known as subnets or CIDR range) can be added to an IP Restriction list.
Accepted formats for IPv4 and IPv6 addresses:
- IP v4 address (e.g.
1.2.3.4) - IP v4 Subnet address (e.g.
1.2.0.0/24) - IP V6 address (e.g.
2001:0DB8:ABCD:0012:0000:0000:0000:0000) - IP V6 condensed notation (e.g.
2001:DB8:ABCD:12::) - IP V6 subnet address (e.g.
2001:db8:abcd:0012::0/64)
Last updated: April 28, 2025